Wpa Handshake Crack
- Posted in:Admin
- 08/03/18
- 42
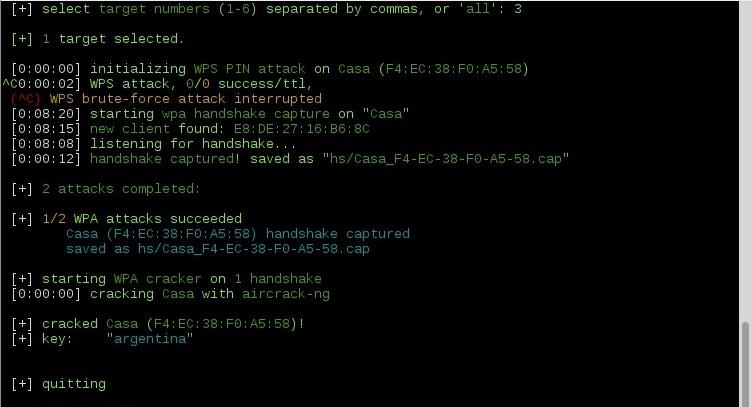
• • • • • • 4 • • • • • Finding the Four-way Handshake To make sure we captured a authentication handshake, we can use the network protocol analyzer (formerly Ethereal). Wireshark allows us to view packet contents and sort by type of packet captured to pull out the WPA handshake. Open up Wireshark ( Backtrack >Privilege Escalation >Sniffers) and open the Kismet capture 'dump' file (Kismet. Gta Vice City Cheats 4 Money. dump) to view all the captured packets. The WPA four-way handshake uses the Extensible Authentication Protocol over LAN (EAPoL). Using Wireshark, we can filter the captured packets to display only EAPoL packets by entering 'eapol' in the filter field (Figure 7). Figure 7: EAPoL filter applied to captured packets Here, we're basically looking for four packets that alternate source, client-AP-client-AP (I've highlighted them in red in Figure 7). Now that we've confirmed that we've captured a four-way handshake it's time to perform the crack.

How exactly does 4-way handshake cracking work? How does handshake cracking work. Why don't we need a WPA handshake on a ARP spoofing MiTM attack? Feb 05, 2018 Hack wpa/wpa2 wifislax linset con handshake phishing y Desautenticacion de clientes. Autocad 2007 Full Crack Sinhvienit Net.