Wireshark Compare Capture Files
- Posted in:Admin
- 19/02/18
- 92
Wireshark will try to merge the packets in chronological order from the dropped files into a newly created temporary file. If you drop only a single file it will simply replace the existing capture. Use the mergecap tool, a command line tool to merge capture files. This tool provides the most options to merge capture files. Comparing two server responses, one bad, one good, is a common way to use Wireshark when troubleshooting an application problem. Clicking through a trace file and noting differences can be difficult, especially when the changes are very subtle.
Is an open source network packet analyzer. Without any special hardware or reconfiguration, it can capture live data going in and out over any of your box's network interfaces: Ethernet, WiFi, PPP, loopback, even USB. Typically it's used as a forensics tool for troubleshooting network problems like congestion, high latency, or protocol errors — but you don't want to wait until your network is in trouble to learn how to use it. This weekend, why not take a look at your network traffic, and learn how to use Wireshark to your advantage? Wireshark is a GTK+ application, although the project also includes a console-based front end named that features most of the functionality found in the GUI version. Software Speedconnect Internet Accelerator V.8.0. Considering its reputation as a useful administration tool, you will probably find it in your distribution's package repositories.
If not, you can packages for several distributions on wireshark.org, along with the source. The current release is 1.4.1.
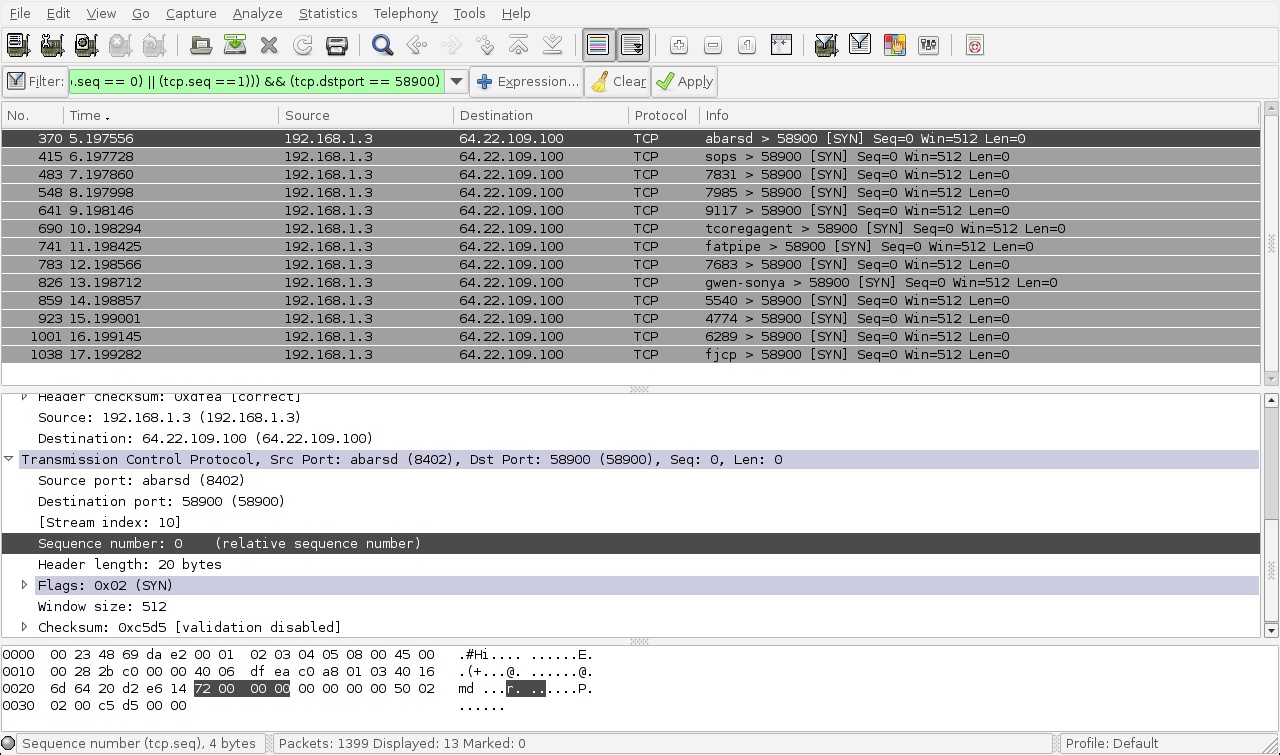
Mac OS X and Windows binaries are available as well, which you may need to analyze machines running those operating systems (more on that later). Because it needs to switch the network interface into ' in order to capture all network traffic, Wireshark must be run as root. The library performs the actual packet capture, and supports a large-but-not-infinite range of network devices. You should check the matrix on the project wiki if you are using a peculiar network type — almost all Ethernet and WiFi cards in common usage will work without incident. Traffic Capture You can start a new network capture session from the 'Capture' menu; Capture ->Interfaces brings up a dialog box showing all of the interfaces Wireshark has detected, plus the pseudo-device 'any' that captures from all of the above. The Capture ->Options choice allows you to specify several options before you begin, including limiting your capture with filtering rules (such as by particular protocols or IP address only), automatically stopping the capture after a specified amount of time, or splitting the file automatically into separate time- or size-dictated files.
Whenever you start your capture, the packets are logged on-screen in a table showing basic information (source and destination, protocol, time, etc.) in column headers. Wireshark color-codes the entries for your convenience by flagging 'interesting' packets, such as TCP retransmissions, with different text and background colors. Siemens Lady Dishwasher Manual.
How long you let your capture run depends on what you need to study. Several hours might be required to catch a hard-to-reproduce problem with an Internet service, but a few minutes' worth will suffice just to familiarize yourself with the tools. After you stop the capture, you can select any packet for further inspection by clicking on it in the log window. How To Install Wifislax On Windows here. The details are displayed in a tree-like sub-window that breaks the packet down by network layer. If you are having Ethernet trouble, you can look into the Ethernet frames; if it is an HTTP problem, you can dig down at that level instead. You should always save captured data that you need for forensic or profiling purposes.
Wireshark uses the.pcap file extension. Do be aware, however, that capture files can get quite large; if you are only interested in a portion of your overall network traffic, you can use Wireshark's filter mechanism — located directly above the main capture table to winnow down the data set before you save it to disk. Examining the Data The filter tool is the most basic way to hone your captured data into useful format. Click the 'Filter' button itself to bring up a selection box with several common options: TCP only, UDP only, everything not to the local IP address, everything-except-DNS-and-ARP, and so forth. Clicking on any of the options in the list will show you the exact filter string in Wireshark's filter syntax, which is a useful way to learn to write your own filter expressions.